Screenshot by way of ZDNet
It’s attainable to compromise Fb accounts utilizing little greater than a cellphone quantity, researchers have warned.
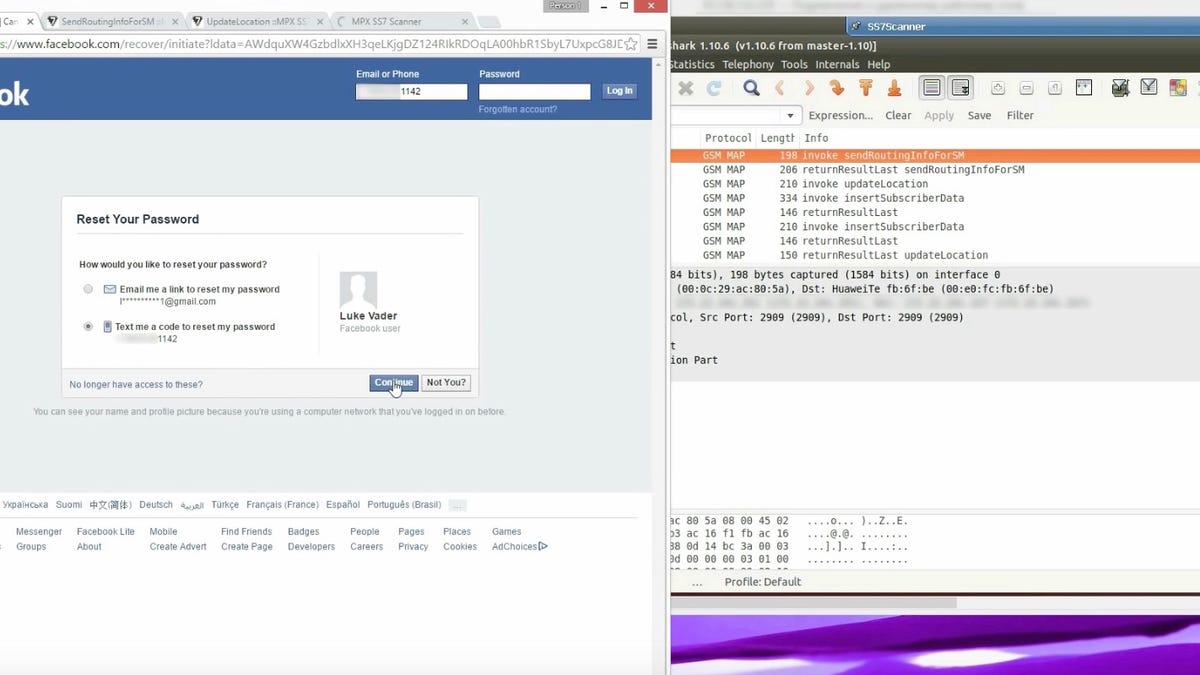
A safety group from Constructive Applied sciences claims that if you recognize the cellphone variety of your supposed sufferer, you’ll be able to break into their linked Fb account due to safety flaws within the SS7 protocol.
As reported by Forbes, there’s a phase of core telecommunications infrastructure which has been left susceptible to use for the final half decade.
SS7 is a protocol developed in 1975 which is used worldwide to outline how networks in a public switched phone community (PSTN) trade data over a digital signaling community. Nonetheless, a community primarily based on SS7 will, by default, belief messages despatched over it — regardless of the place the message originated from.
The safety flaw lies throughout the community and the way SS7 handles these requests, relatively than a bug on Fb’s platform. All cyberattackers must do is to observe the “Forgot account?” process by means of Fb’s homepage, and when requested for a cellphone quantity or electronic mail tackle, supply the official cellphone quantity.
As soon as Fb has despatched alongside an SMS message containing the one-time code used to entry the account, the SS7 safety flaw can then be exploited to divert this code to the attacker’s personal cell system, granting them entry to the sufferer’s account.
Constructive Applied sciences supplied a proof-of-concept (PoC) video demonstrating the assault, which could be seen under:
The sufferer will need to have linked their cellphone quantity to the goal account, however because the safety flaw is discovered throughout the telecommunications community and never on-line domains, this assault may also work in opposition to any internet service which makes use of the identical account restoration process — resembling Gmail and Twitter.
Two-step verification is changing into an increasing number of essential, however till vulnerabilities in telecom companies are fastened, utilizing electronic mail restoration strategies could also be one of the simplest ways to go — in addition to the usage of very sturdy, advanced passwords for any most important ‘hub’ electronic mail accounts you employ to keep up different on-line companies.
Final-minute low cost tech devices and items for Father’s Day 2016